A new variant of the Crypto Ransomware has begun to spread, targeting Australia and New Zealand.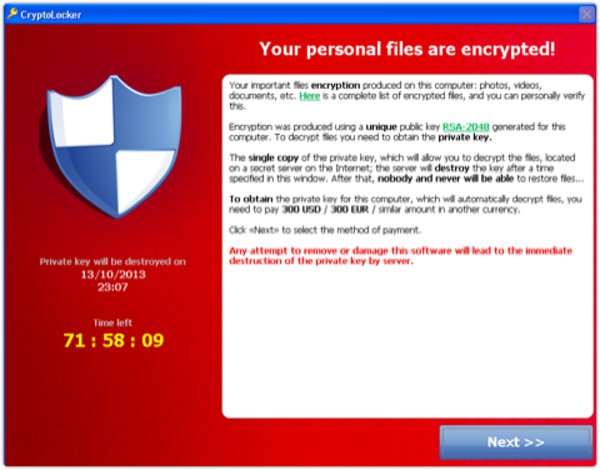
While most malware is detected and identified in more dense areas of the world before it hits Australia and New Zealand, the latest Crypto malware is designed to specifically fool and infect the Oceanic region.
Once the virus infects the target machine, it automatically starts to encrypt non-system data, deletes itself from the machine to avoid being identified for later signatures, and sends the decryption key to a remote server in case the customer is willing to pay for decryption.
A mixture of End User Education and an effective Active Virus program is your best defence to avoid infection and damage. Since the malware is constantly evolving and its infection target is small, signatures for the variants are not a reliable method of detection.
To improve and qualify protection for your business we recommend:
- Active Virus Control (AVC) module is enabled and runs at no lower than Normal (Default) or Aggressive.
- Disable the display of Alert Popups to avoid your end users allowing the execution of the Ransomware.
- Make use of the free Crypto Vaccine from Bitdefender – this runs alongside your current Anti-Virus but doesn’t replace it.
- MOST IMPORTANTLY – Educate End Users on safe internet practices!
Most malware currently relies on human interaction to enter the system.
So do not:
- Click on any suspect emails
- Open attachments from emails (especially those that you are not expecting)
- Agree to allow the malware to run by overriding the Notification Pop Ups – which may allow the malware to run for a period of time before you are aware that it has infiltrated your computer.
To protect against these types of infection, schedule continuous file backups (either locally or in the cloud) so data can be recovered in case of corruption.
To be secure, local backups must be offline (not connected to the computer), if they are commected to the computer they may also be encrypted and made useless. Any backup that you can browse around the backup drive and see your files will be encrypted if you get one of these infections.
Cloud backups like Carbonite, etc should be safe from the malware because they often keep multiple versions of the files.
What if you've been infected by one of the ransomware variants?
You have a couple of options:
- Restore from your most current backup. Assuming that you have one.
- Restore from shadow copies, if this option has been enabled. If you don't know what shadow copies are or your files are not on a File Server then you probably dont have this enabled.
- The last resort is to pay the fee. Although keep in mind that there are agencies who are always on the lookout for these scammers and regularly take down their servers. This may mean that you could pay the fee and still not get your data back.
If you want more information or require assistance just contact us.

